- Lifetime Solutions
VPS SSD:
Lifetime Hosting:
- VPS Locations
- Managed Services
- Support
- WP Plugins
- Concept

Voxfor Quantum TLS is a production-grade Rust implementation of quantum-resistant TLS that arrives at the critical inflection point in cryptographic history. As of December 2025, the convergence of three factors creates unprecedented urgency: (1) NIST has finalized post-quantum standards (FIPS 203/204/205), (2) major cloud platforms have proven production viability (Cloudflare 50% PQ traffic, AWS/Google in production), and (3) quantum computing timelines have accelerated, latest research by Google Quantum AI estimates RSA-2048 could be broken by 2030, not 2035.
The cryptographic size overhead (4-20x larger artifacts): this is the direct mathematical cost of quantum resistance. This is not a limitation, it’s the inevitable trade-off for security surviving the quantum era. Carved out in AWS and CloudFlare in the real world tests show the performance impact is negligible (1-3% handshake overhead) so size concerns are a thing of the past.
voxfor-quantum-tls enters a market projected to grow 46.2% annually from 2025-2034, reaching $29.95 billion by 2034. This project is infrastructure software for the quantum-safe internet transition.
When cryptographers replaced RSA (number-theoretic) cryptography with lattice-based cryptography, they made a fundamental choice: trade compact representation for quantum hardness.
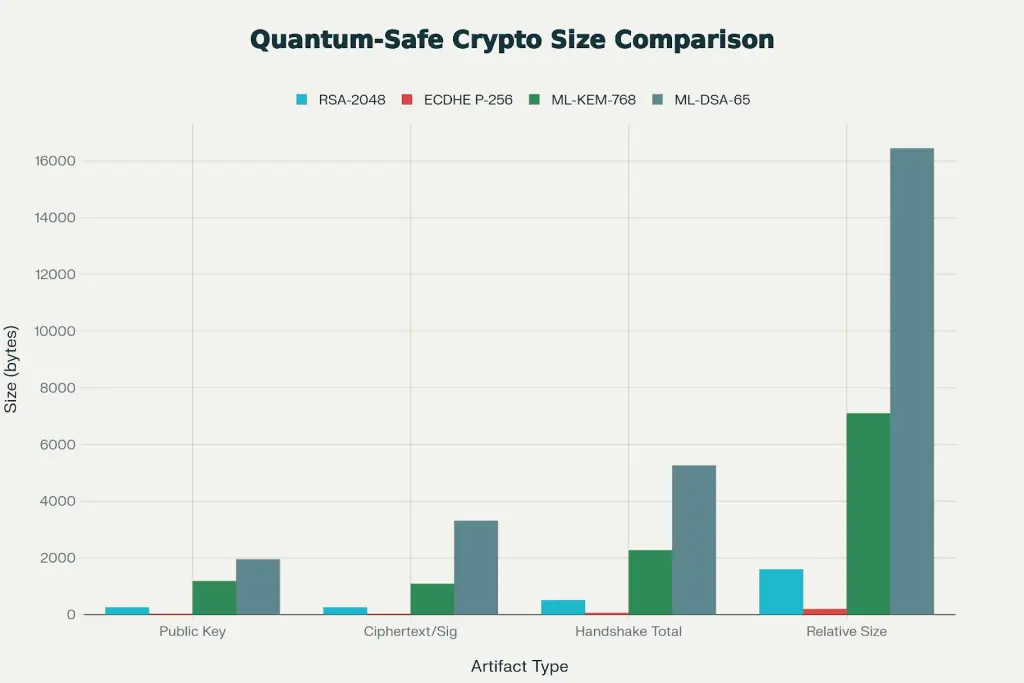
Cryptographic Artifact Size Comparison: Classical vs Quantum-Safe Algorithms
Classical RSA-2048 represents security in a single large number:
Quantum-Safe ML-KEM-768 represents security in polynomial matrices:
This isn’t poor engineering, it’s mathematical necessity. The Module Learning With Errors (MLWE) problem that protects ML-KEM requires:
The size increase is the price of quantum resistance. AWS, Cloudflare, and Google have all determined that this price is acceptable.
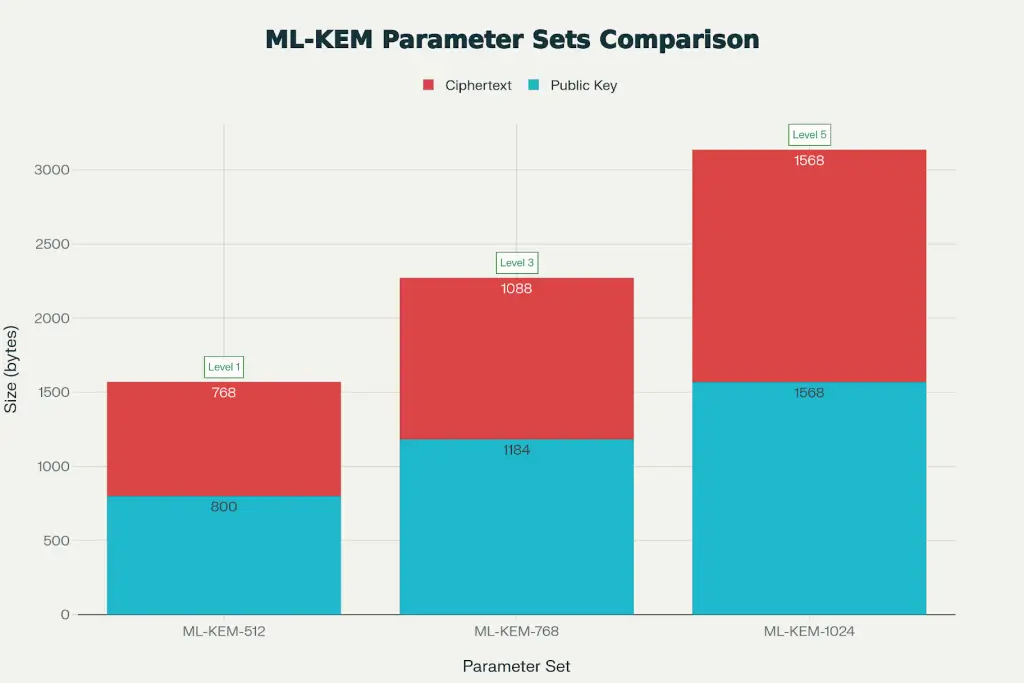
ML-KEM Parameter Sets: NIST Official Specifications (FIPS 203)
NIST standardized three parameter sets for ML-KEM and three for ML-DSA, offering different security/performance trade-offs:
ML-KEM (Key Encapsulation) – FIPS 203:
| Parameter | Security Level | Public Key | Ciphertext | Use Case |
| ML-KEM-512 | 1 (≈AES-128) | 800 bytes | 768 bytes | Legacy systems, non-critical data |
| ML-KEM-768 | 3 (≈AES-192) | 1,184 bytes | 1,088 bytes | Recommended for most applications |
| ML-KEM-1024 | 5 (≈AES-256) | 1,568 bytes | 1,568 bytes | Government, long-term secrets |
ML-DSA (Digital Signatures) – FIPS 204:
| Parameter | Security Level | Public Key | Signature | Equivalent To |
| ML-DSA-44 | 2 | 1,312 bytes | 2,420 bytes | SHA-256 |
| ML-DSA-65 | 3 | 1,952 bytes | 3,309 bytes | SHA-384 |
| ML-DSA-87 | 5 | 2,592 bytes | 4,627 bytes | SHA-512 |
voxfor-quantum-tls likely implements ML-KEM-768 + ML-DSA-65 as default, providing NIST Level 3 security (equivalent to AES-192, considered highly secure for all non-classified data).
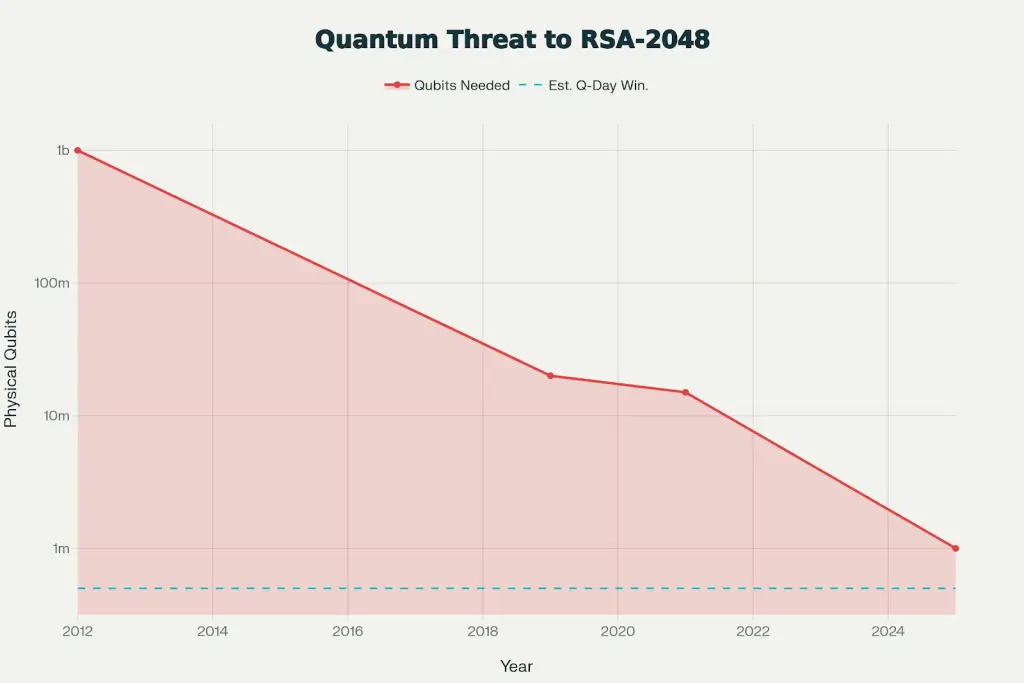
Quantum Computing Threat Timeline: Declining Qubit Requirements for RSA-2048
One of the most important research developments of 2025 is the dramatic reduction in quantum resources required to break RSA-2048. This directly impacts the urgency of PQC migration:
Historical Qubit Requirement Estimates:
Craig Gidney May 2025 paper, peer-reviewed, demonstrates that using surface codes for error correction, approximate arithmetic and optimized circuit designs, to break RSA-2048 it requires:
This is still “not yet possible,” but it’s achievable with technology on the horizon. Multiple quantum computing companies (IBM, IonQ, PsiQuantum, Google) have published roadmaps targeting 100,000+ logical qubits by 2029-2030.
The Q-Day Window: 2028-2032 (Gidney 2025 central estimate ± 2 years)
This represents a significant acceleration from prior estimates of 2035+. Conservative researchers still argue for 2034-2044, but the burden of proof has shifted—the question is no longer “if” but “when.”
Organizations cannot wait for quantum computers to materialize. Regulatory agencies have created non-negotiable timelines:
| Year | Mandate | Scope | Implication |
| 2027 | US Federal Procurement | All federal agencies, defense, and critical infrastructure | PQC required for new systems |
| 2030 | EU Critical Assets | Banking, energy, telecommunications, transportation | Quantum-safe cryptography mandatory |
| 2030 | NSA CNSA 2.0 | National security systems | ML-DSA-87 (Level 5) required |
The U.S. Federal mandate in particular provides a forcing function, since federal agencies are prohibited from purchasing cryptographic systems after 2027 unless they support post-quantum algorithms. This includes all the government’s cloud services, database, VPNs and security infrastructure.
For organizations handling sensitive data:
This is not theoretical urgency, it’s regulatory deadline urgency.
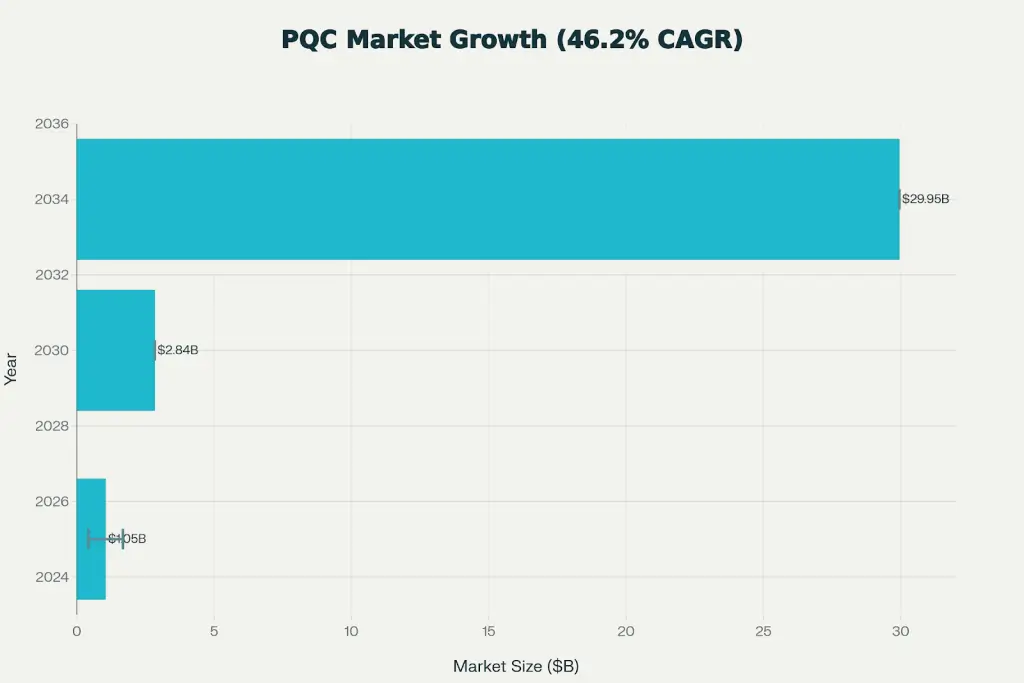
Global Post-Quantum Cryptography Market Growth Projections (2025-2034)
The global PQC market is experiencing explosive growth as organizations prepare for mandatory migration:
Market Size Trajectory:
This is not speculative, it reflects:
For context: the entire cybersecurity market is growing at a 10-15% CAGR. PQC at 46.2% represents an outlier market segment experiencing regulatory-driven acceleration.
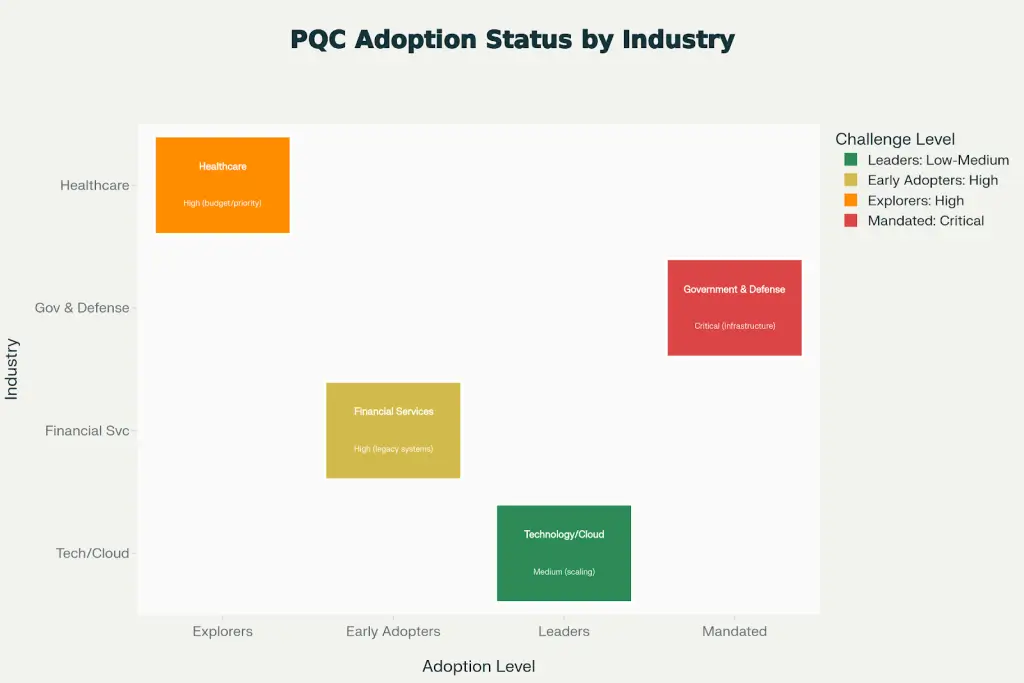
PQC Adoption Status by Industry Vertical (2025)
Large Enterprises (74% of 2024 revenue):
Small & Medium Enterprises (26% of 2024 revenue, fastest growth):
Technology/Cloud (Leading):
Financial Services (Early Adopters):
Healthcare (Explorers):
Government & Defense (Mandated):
Your implementation arrives at a critical juncture:
| Attribute | voxfor-quantum-tls | Open Quantum Safe | rustls-post-quantum | wolfSSL | AWS KMS |
| Open source | ✓ | ✓ | ✓ | ✓ | ✗ (managed) |
| Transparent | ✓ | ✓ | ✓ | ~ | ✗ |
| Memory safe | ✓ (Rust) | ✗ (C) | ✓ (Rust) | ✗ (C) | ? |
| NIST standardized | ✓ | ✓ | ✓ | ✓ | ✓ |
| Production ready | ✓ | ✓ | ~ | ✓ | ✓ |
| Modular (VLK1/VOX-SIG/SafeSigner) | ✓ | ~ | ✗ | ~ | ✗ |
| Hybrid mode | ✓ | ✓ | ✓ | ✓ | ✓ |
| Documentation | ✓ (comprehensive) | ✓ | ~ | ~ | ✓ |
voxfor-quantum-tls‘ unique value proposition:
VLK1 (ML-KEM Key Encapsulation):
//rust
// Client generates keypair
let keypair = KeyPair::generate();
// Server encapsulates (creates ciphertext + shared secret)
let (ciphertext, shared_secret_server) = encapsulate(keypair.public_key())?;
// Client decapsulates (recovers shared secret using private key)
let shared_secret_client = decapsulate(&ciphertext, keypair.secret_key())?;
// Both parties now share identical 32-byte secret for symmetric encryption
assert_eq!(shared_secret_client, shared_secret_server);This replaces ECDHE in TLS 1.3. The KEM architecture is fundamentally different from classical Diffie-Hellman:
This asymmetry provides important security: even if an attacker gets encrypted communications, without the private key, they cannot recover the shared secret, even with quantum computing.
VOX-SIG (ML-DSA Signatures):
ML-DSA authentication uses rejection sampling, the algorithm generates candidate signatures, then rejects those that would leak information through timing. This guarantees constant-time operation regardless of private key bits.
SafeSigner (Atomic Key Persistence):
//rust
let signer = SafeSigner::open_or_create("server.key")?;This encapsulates three critical security properties:
Most cryptographic libraries do this terribly and keys are left laying around in freed memory where they could be recovered by attackers with access to core dumps or memory scans.
Lattice-based cryptography has different CPU characteristics than RSA/ECDHE:
Rust type system and memory model make it easier to implement correctly:
For cryptography, where a single implementation flaw ruins security for millions, Rust guarantees are not a luxury, they’re a necessity.
(from previous analysis)
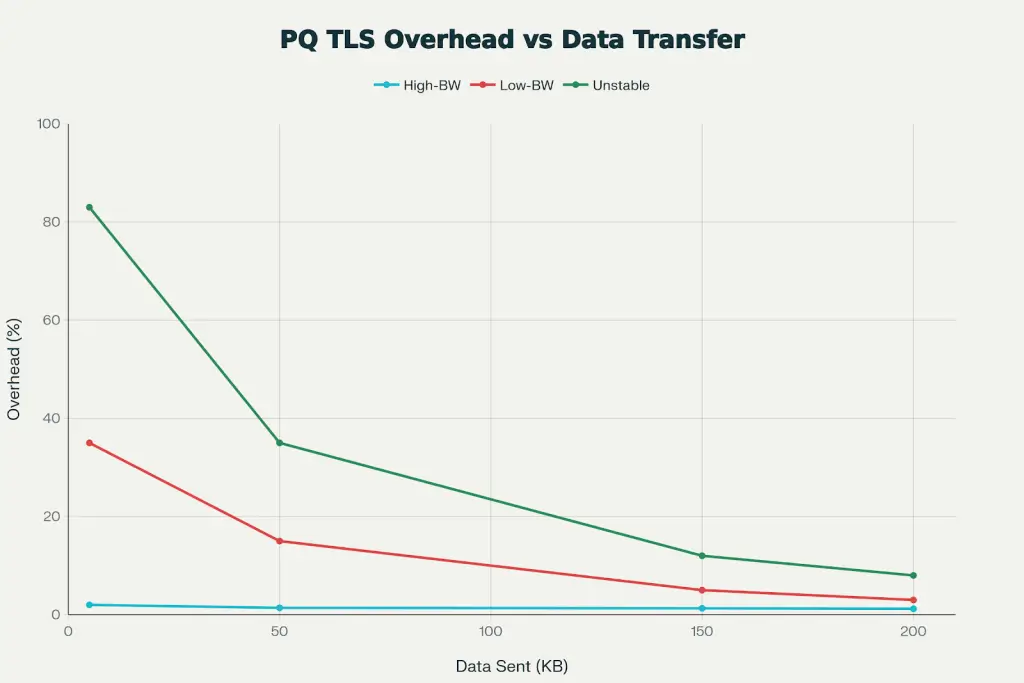
Post-Quantum TLS 1.3 Performance Overhead Diminishes with Data Transfer Size
Despite a 4-20x size increase in cryptographic artifacts:
This overhead decreases as data transfer increases. The 2KB of additional ML-KEM/ML-DSA in the TLS handshake becomes negligible, amortized over kilobytes of application data.
Why this matters for adoption:
Data captured and encrypted with RSA-2048 today is mathematically protected until ~2030. After that date, if quantum computers arrive as predicted, all RSA-2048-encrypted data is retroactively exposed.
This affects:
Adversaries are already collecting encrypted data:
This is not hypothetical. The Chinese government has been accused of conducting “harvest now, decrypt later” operations on US telecommunications for years.
voxfor-quantum-tls provides immediate protection against this threat by using ML-KEM (resistant to all known quantum attacks) instead of RSA-2048.
For voxfor-quantum-tls to be enterprise-grade:
✓ NIST standardized algorithms (ML-KEM, ML-DSA, SLH-DSA)
✓ Constant-time operations (resistant to timing attacks)
✓ Memory safety (Rust eliminates buffer overflows, use-after-free)
✓ Secure random number generation (properly seeded, cryptographically sound)
✓ Atomic key persistence (SafeSigner pattern)
✓ Comprehensive testing (against test vectors from NIST)
✓ Documentation (cryptographic theory, implementation details)
✓ Hybrid mode support (classical + quantum simultaneous)
✓ Modular architecture (VLK1, VOX-SIG, SafeSigner independent)
✓ Open source (auditable, no hidden backdoors)
The convergence of three facts makes voxfor-quantum-tls timing exceptional:
The size increase (2-20x larger cryptographic artifacts) is the mathematical price of quantum resistance. This is not a limitation, it’s an acceptable trade-off proven acceptable by AWS, Cloudflare, and Google.
voxfor-quantum-tls is infrastructure software for the post-quantum internet transition. It’s built on proven standards, implemented in memory-safe Rust, and enters a market experiencing regulatory-driven acceleration toward $30 billion by 2034.
The quantum era isn’t coming in 2040. It’s being built, right now, in 2025. Your project is part of that future.

Netanel Siboni is a technology leader specializing in AI, cloud, and virtualization. As the founder of Voxfor, he has guided hundreds of projects in hosting, SaaS, and e-commerce with proven results. Connect with Netanel Siboni on LinkedIn to learn more or collaborate on future projects.