- Lifetime Solutions
VPS SSD:
Lifetime Hosting:
- VPS Locations
- Managed Services
- Support
- WP Plugins
- Concept

This is one of the basic security measures that enable the encryption of user-sensitive data in order to avoid unauthorized access and malicious methods. At a time when data breaches have a catastrophic impact, including both legal fees and financial fines, and per the reputation of the organization, which is hard to fix, the use of strong password encryption is not a luxury anymore; it is a necessity for any app that requires users to enter their data.
You can be creating a simple WordPress mobile and can be working on an enterprise application. Still, you can use the knowledge of the PHP password encryption techniques to use the industry best practices of ensuring user privacy and adhering to data protection laws. This is a detailed tutorial covering the basics of encryption, the encryption options offered by the PHP language, how to use them most efficiently, and an example of a working code that will assist you in the process of password protection.

PHP password encryption is a security methodology, that involves the encryption of plaintext passwords that are readable to unreadable encrypted texts (ciphertext) by applying mathematical algorithms and only after the application of certain decryption keys or verification procedures.
Encryption operates through a series of fundamental steps:
This process ensures that even if a hacker gains database access, they cannot read user passwords directly. Common real-world examples include HTTPS encryption protecting client-server communication and SSL certificates securing sensitive transactions.
Password encryption forms the cornerstone of modern application security for several compelling reasons:
Unless it is appropriately encrypted, any breached database can be left in plaintext with all user passwords disclosed. Attackers can then use them to:
Laws such as GDPR, CCPA, HIPAA and PCI DSS specifically require the encryption of passwords and secure data management. Non-compliance results in:
Data breaches involving unencrypted passwords cause:
Strong security is a mandatory service that modern users expect. Such applications that do not have proper password encryption are considered careless and incompetent, which directly affects user acquisition and retention.
Secure password encryption follows a standardized process designed to maximize security and prevent unauthorized decryption:
Create a Data Encryption Key (DEK), a unique cryptographic key used specifically for encrypting the password. This key should be generated using cryptographically secure random number generators.
Use the DEK to encrypt the plaintext password through the selected encryption algorithm, producing the encrypted ciphertext.
Send the DEK to a Key Management Service (KMS) like Google Cloud KMS, which encrypts it using its own Key Encryption Key (KEK). This two-tier approach ensures that even if someone accesses encrypted passwords, they cannot decrypt them without the KEK.
Store the encrypted password and the KEK in the database in such a way that they are related to each other, and neither can be used without the other.
Delete the original DEK from memory to prevent it from being recovered through memory forensics or other attack techniques.
This multi-layered approach creates security depth, multiple barriers an attacker must overcome to compromise a single password.
MySQL handles password encryption internally through specific functions, but developers should understand its limitations and superior alternatives.
MySQL provides the Password() function for encrypting passwords, which automatically executes when you create new user accounts using the CREATE USER command. However, this function has significant limitations:
Instead of relying on the MySQL Password() function, implement stronger encryption methods at the application level:
The most important concept is to add a random salt to each password, which will not allow the attackers to crack several passwords at once with some pre-computed rainbow tables.
There are a few encryption methods presented in modern PHP development, and each has its own application, advantages, and security features.
What is hashing?
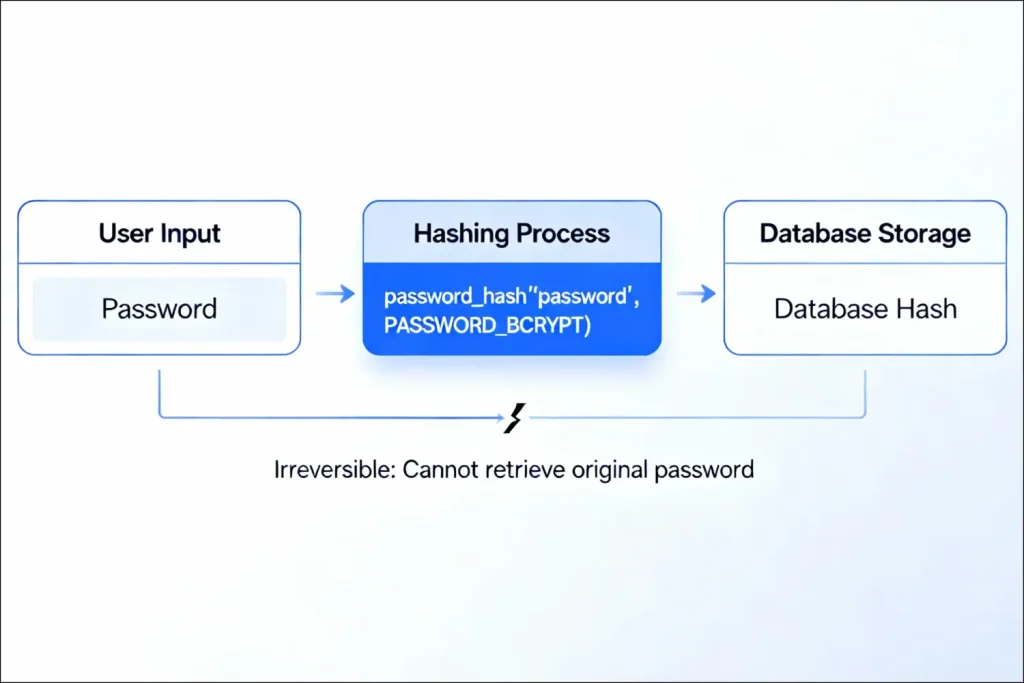
Hashing is a one-way encryption technique that transforms plaintext into a predetermined length of characters (hash), which cannot be inverted to obtain the original password. In contrast with symmetric encryption, a hash is irreversible in nature, and it has no key.
How hashing protects passwords:
In case the hacker has access to the database, they see a hash value that cannot be read. Even when the hash is used, it takes tremendous computing resources to brute force the original password, and when hashing is implemented correctly, attacks of this nature are infeasible.
The password_hash() function
PHP password_hash() function represents the gold standard for password hashing, utilizing bcrypt, a deliberately slow hashing algorithm specifically designed for password security.
Key advantages of password_hash():
Example: Hashing a password with password_hash()
<?php
// Define the plaintext password
$unencrypted_password = "Cloudways@123";
// Hash the password using bcrypt (PASSWORD_DEFAULT)
$hash = password_hash($unencrypted_password, PASSWORD_DEFAULT);
// The hash can be safely stored in the database
echo "Generated hash code: " . $hash;
// Output: $2y$10$LZExuh/rXamd/X5yuDatn.L8ROlKBry3xidvWc.O19nx85.CrSrO.
?>The output demonstrates hash complexity, even the same password hashed multiple times produces different results due to the included salt.
Why you cannot read hashed passwords
Stored passwords should never be read, even by the owner of the website. Such a designed principle is necessary to make sure that in case a person gets access to your accounting account/they cannot crack the user passwords. The account recovery exercise should be employed by the user at all times to obtain entry into the account, and this can be done in a way that is secure way.
What is symmetric encryption?
Secret Key Encryption (also called Symmetric Encryption) uses a single shared key for both encrypting and decrypting data. The sender encrypts data with the key, and the recipient decrypts it using the identical key.
How symmetric encryption works:
Advantages of symmetric encryption:
Critical vulnerability: Key distribution problem
Symmetric encryption has a great risk: how to share the key securely with the sender and recipient. In case the key is relayed on a non-secure network, an attacker can capture the key and then decrypt all the data that is encrypted. Symmetric encryption is inappropriate for:
Best practices for symmetric encryption:
What is envelope encryption?
Envelope encryption combines symmetric and asymmetric encryption techniques to achieve the performance benefits of symmetric encryption with the security advantages of asymmetric encryption.
How envelope encryption works:
Envelope encryption process visualization:
Advantages of envelope encryption:
Implementing with Cloud KMS
Google Cloud Key Management Service (KMS) and similar services automate envelope encryption:
This approach provides enterprise-grade security while remaining accessible to developers.
Practical implementation of password encryption requires understanding PHP native functions and best practices.
The password_hash() function provides the most secure and straightforward password encryption method for PHP applications.
Syntax:
string password_hash(string $password, int|string|null $algo, array $options = []): stringParameters:
Complete password hashing example:
<?php
// 1. Get the plaintext password from user input (sanitized)
$unencrypted_password = $_POST['password'];
// 2. Hash the password using bcrypt with default options
$hash = password_hash($unencrypted_password, PASSWORD_DEFAULT);
// 3. Store the hash in the database (NOT the plaintext password)
// Example: $mysqli->query("INSERT INTO users (email, password) VALUES ('$email', '$hash')");
// Output example
echo "Generated hash code: " . $hash;
// Output: $2y$10$LZExuh/rXamd/X5yuDatn.L8ROlKBry3xidvWc.O19nx85.CrSrO.
?>Important considerations:
When users log in, verify their entered password against the stored hash using the password_verify() function rather than comparing hashes directly.
Syntax:
bool password_verify(string $password, string $hash): boolParameters:
Returns:
Complete password verification example:
<?php
// 1. Get the plaintext password from user login form
$entered_password = $_POST['password'];
// 2. Retrieve the hashed password from database
// Example: $result = $mysqli->query("SELECT password FROM users WHERE email='$email'");
// Example: $user = $result->fetch_assoc();
$stored_hash = "$2y$10$LZExuh/rXamd/X5yuDatn.L8ROlKBry3xidvWc.O19nx85.CrSrO.";
// 3. Verify the entered password against the stored hash
$verify = password_verify($entered_password, $stored_hash);
// 4. Check verification result and handle login accordingly
if ($verify) {
echo 'Correct Password!';
// Start user session, set cookies, redirect to dashboard
} else {
echo 'Password is Incorrect';
// Log failed attempt, show error message
}
?>Security best practices for password verification:
To achieve better security or tighter demands, set the parameter of the cost of bcrypt to a higher value to slow down the hashing process (be less susceptible to brute force):
<?php
// Increase cost parameter for slower hashing (higher security)
$options = [
'cost' => 12 // Default is 10, increasing to 12 doubles hashing time
];
$hash = password_hash($unencrypted_password, PASSWORD_BCRYPT, $options);
?>Cost parameter guidelines:
The cost parameter should increase as hardware becomes faster, ensuring hashing remains computationally expensive enough to prevent practical brute force attacks.
| Method | Speed | Reversibility | Use Case | Security Level |
| password_hash() (bcrypt) | Medium | No (one-way) | User passwords | Excellent |
| Secret Key (symmetric) | Very fast | Yes (reversible) | Data encryption | Good (if key is secure) |
| Envelope encryption | Medium | Yes (reversible) | Sensitive data at scale | Excellent |
| MD5 | Very fast | Yes (crackable) | Legacy only (NOT recommended) | Poor |
| SHA1 | Very fast | Yes (crackable) | Legacy only (NOT recommended) | Poor |
| SHA256 + salt | Fast | Yes (reversible) | General hashing | Good |
Always use the PHP password_hash() function for password encryption. Avoid deprecated methods like md5(), sha1(), or crypt(), which are cryptographically broken.
Never store plaintext passwords under any circumstances. Hashes are the only appropriate password storage method.
Hash passwords on the server-side after HTTPS transmission. This prevents attackers from intercepting passwords during transmission.
Rely on password_hash() automatic salting rather than manual salt generation, which often contains security flaws.
Even administrators should not be able to read stored passwords. Implement password reset functionality instead.
Prevent brute force attacks by limiting login attempts:
Require additional verification beyond passwords for sensitive operations:
Conduct periodic security assessments:
PHP password encryption is not optional in modern application development, it’s a fundamental security requirement that protects user privacy, ensures regulatory compliance, and maintains customer trust. The landscape of password encryption has evolved significantly, with modern best practices favoring one-way hashing using algorithms like bcrypt over outdated methods like MD5 or SHA1.
By implementing the practices outlined in this guide, particularly using password_hash() for all new development, you ensure your PHP applications provide the security users expect and regulations require. The fact that proper password hashing is only slightly more costly than the cheap hash mechanism is nothing in comparison to the importance of security, and it is therefore a mandatory component of professional PHP programming.

Hassan Tahir wrote this article, drawing on his experience to clarify WordPress concepts and enhance developer understanding. Through his work, he aims to help both beginners and professionals refine their skills and tackle WordPress projects with greater confidence.