- Lifetime Solutions
VPS SSD:
Lifetime Hosting:
- VPS Locations
- Managed Services
- Support
- WP Plugins
- Concept

The digitization of the digital ecosystem in 2026 has impacted the security of websites, moving it from a marginal technical issue to the core organization of stability and trust of consumers. With the world economy continuously shifting to web-based technology, malicious activities have been more sophisticated and prevalent than ever before. Statistics show that there is a yearly growth of 18% of cyber-attacks, and the cost of cybercrime is estimated to be more than $10.5 trillion on an annual basis.
This amplification of the threat environment, commoditization of hacking tools, and weaponization of artificial intelligence are motivated by the geopolitical instability convergence. It is not possible to secure a site through reactive patching in this age; it needs a multi-layered architecture that brings together cryptographic integrity, stringent identity control, and a culture of operational vigilance.
The current environment is characterized by a strategic pivot among cybercriminals toward the exploitation of human trust. Traditional brute-force attacks are increasingly being supplemented, and in many cases replaced, by “callback phishing” and other forms of social engineering that bypass automated security scanners by leveraging direct human interaction. At the same time, the expansion of the so-called Shadow AI and AI-native malware has added another dimension of interference, where the opponent can produce polymorphic code that is not detected by the usual signature method. In this regard, the process of keeping websites secure should be perceived as a dynamic lifecycle and not as a fixed setup.
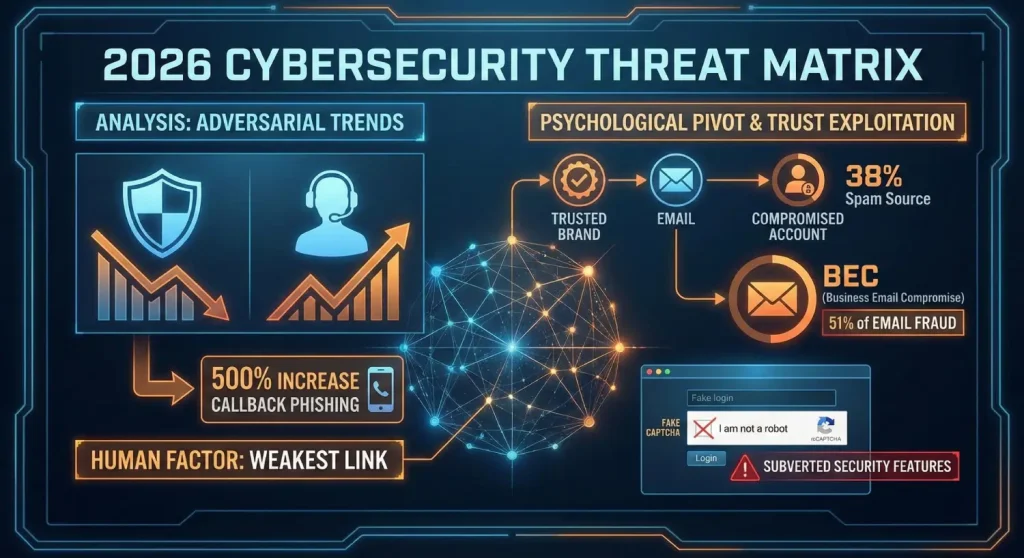
The strategic environment of cybersecurity in 2026 will be characterized by the accelerated rate of changes in attack vectors that aim at undermining the basis of trust within the internet. The VIPRE Q4 2025 Email Threat Trends Report notes that there was a shocking 500% increase in callback phishing, as threat actors no longer use malicious links to attack victims, but instead mislead them into making phone calls or initiating a chat session. This change highlights a larger trend: the human factor has become the weakest link in security as technical security gets more difficult to breach.
Cybercriminals have become adept at using legitimacy as a weapon. During late 2025 and into 2026, compromised legitimate accounts became the primary source of spam, representing 38% of such deliveries. By infiltrating trusted brands or executive accounts, a practice known as Business Email Compromise (BEC), attackers can bypass traditional email filters that rely on reputation scores. BEC currently accounts for 51% of all email fraud cases, demonstrating the immense financial success of impersonation-based campaigns.
Furthermore, security features designed to protect users are being subverted. Fraudulent login screens nowadays are often defended with fake CAPTCHA and “I am not a robot” checks by attackers. These features have two purposes: to prevent automated security crawlers from identifying the phishing site, and to give the user a false sense of security, as users often view these recognizable security indicators as proof of a valid site.
The integration of artificial intelligence into the hacker’s toolkit has fundamentally altered the pace of cyber conflict. Generative AI models are now used to produce polymorphic malware that alters its own code to avoid detection by antivirus software. Moreover, deepfake technology is being utilized for “Fraud-as-a-Service” (FaaS), allowing low-skill actors to impersonate the voices and faces of executives to authorize fraudulent transactions.
Beyond AI, the specter of quantum computing has moved from a theoretical concern to a strategic priority. Predictions for 2026 suggest that the industry is reaching a turning point where quantum readiness must be addressed to protect against “harvest now, decrypt later” (HNDL) attacks, where adversaries steal encrypted data today in anticipation of being able to break current encryption standards with future quantum hardware.
| Threat Category | Primary Mechanism | Strategic Impact in 2026 |
| Callback Phishing | Direct human interaction/support calls. | 500% growth; evades automated scanning. |
| BEC / Whaling | Executive impersonation. | 51% of email fraud targets financial authority. |
| Quishing | Malicious QR code redirection. | 25% YoY increase; exploits physical trust. |
| Shadow AI | Unauthorized AI tool usage. | Emerging top threat: creates unmonitored data leaks. |
| Ransomware 2.0 | Data exfiltration and encryption. | Record activity; shift to “double extortion”. |
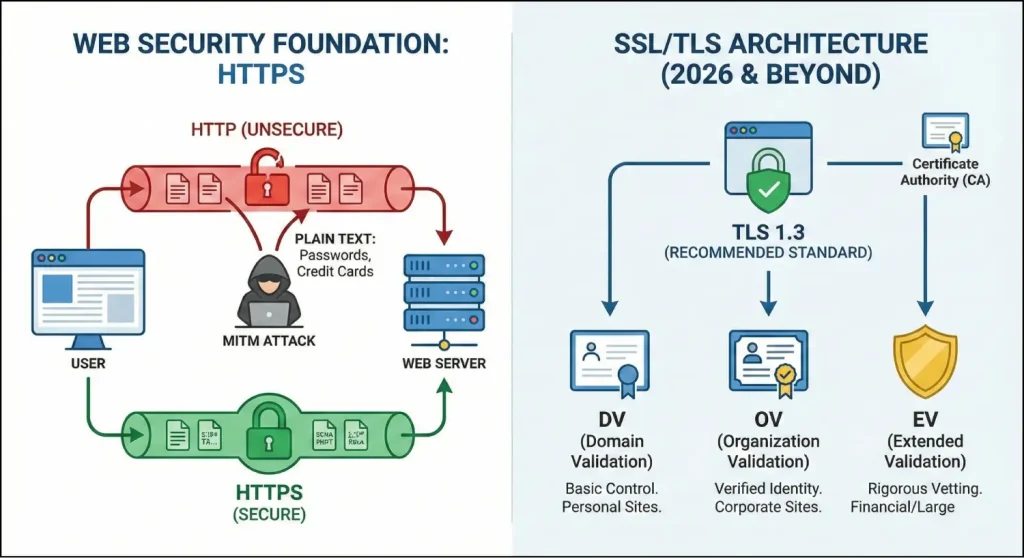
The first line of defense for any web asset is the establishment of a secure communication channel. Hypertext Transfer Protocol Secure (HTTPS) is the modern standard for ensuring data confidentiality and integrity between a client’s browser and the web server.
Without HTTPS, data such as passwords, credit card numbers, and personal identifiers are transmitted in plain text, making them susceptible to interception via man-in-the-middle (MITM) attacks.
Secure Sockets Layer (SSL) and its successor, Transport Layer Security (TLS), are the protocols that enable HTTPS. As of 2026, the implementation of TLS 1.3 is the recommended standard, offering faster handshakes and improved security by eliminating outdated cipher suites.
The efficacy of these certificates depends on the level of validation performed by the Certificate Authority (CA).
It is not enough to install a certificate. To avoid downgrade attacks, administrators will be required to implement secure protocols. HSTS (HTTP Strict Transport Security) is an essential feature, and it teaches the browsers to communicate with a site using HTTPS within a given time frame. It means that attackers cannot force a browser to make use of an unencrypted HTTP connection.
Furthermore, cookie security is paramount. Cookies must be configured with the Secure attribute to ensure they are only sent over encrypted connections, and the HttpOnly attribute to prevent client-side scripts from accessing them, which is a primary defense against session hijacking.
Weak or compromised credentials remain the single largest vulnerability in website security. Statistical evidence indicates that 82% of malicious file attacks are delivered via email, often aimed at harvesting credentials. In 2026, the industry is shifting away from reliance on passwords toward more resilient authentication methods.
The FIDO2/WebAuthn standards enable passkeys to be a quantum leap in security. Passkeys, unlike passwords, employ public-key cryptography. The user has a private key stored on their device, secured by biometrics or device PIN, and it is never shared with the web.
The passkeys in this architecture are necessarily immune to phishing due to the lack of a secret that an attacker can steal or guess. Major corporations, such as Microsoft, Google, and Apple, have incorporated passkey support, allowing administrators to create global accounts with a biometrically protected, passwordless log-in.
Multi-Factor Authentication (MFA) is a must in an environment where passwords are still utilized. Nevertheless, not every MFA technique is equal. By 2026, security experts will use phishing-resistant MFA (e.g., hardware security keys, such as YubiKey; or authenticator apps, e.g., Google Authenticator, Authy) instead of an SMS-based code, which may be intercepted by SIM-swapping or vishing.
Administrative access should follow the Principle of Least Privilege (PoLP). This entails granting users only the specific permissions required for their roles and strictly limiting the number of global administrator accounts. Role-Based Access Control (RBAC) allows for the granular management of these permissions, ensuring that an editor, for example, cannot modify server-level configurations.
| Authentication Method | Security Level | Resistance to Phishing | Implementation Cost |
| Single-Factor (Password) | Low. | None. | Low |
| MFA (SMS-based) | Moderate. | Low. | Low |
| MFA (Authenticator App) | High. | Moderate. | Low |
| Passkeys (FIDO2) | Very High. | High. | Low to Moderate |
| Hardware Security Key | Maximum. | Maximum. | Moderate |
To offer security to web applications, a perimeter is necessary to block the entry of malicious intent, even before it gets to the server infrastructure. The Web Application Firewall (WAF) is the main tool to this end, and it is a kind of gatekeeper, which will examine traffic on incoming HTTP requests to identify malicious patterns, including SQL injection (SQLi), Cross-Site Scripting (XSS), or local file inclusion (LFI).
WAF solutions are generally categorized into DNS-level (cloud-based) and endpoint-based (on-site) systems.
Cloud-based firewalls, such as those provided by Cloudflare and Sucuri, intercept traffic at the network’s edge, preventing malicious requests from ever reaching the web server. This is particularly effective for mitigating large-scale DDoS attacks.
The 2026 DDoS attacks have also become more diverse, with volumetric floods (where the attacker tries to saturate the network bandwidth) and application-layer attacks (where the attacker targets certain server resources, like database search functionality).
Tolerance to these threats has been placed on the so-called always-on mitigation mechanisms, which are capable of detecting and absorbing the abnormal traffic bursts. An important aspect of this defense is rate limiting, which enables an administrator to limit the quantity of requests that a single IP address is permitted to make within a specified period of time.
The strategy for securing a website must be tailored to the underlying platform. Each ecosystem presents unique vulnerabilities and provides different tools for mitigation.
WordPress remains the most targeted CMS due to its extensive use. Security in WordPress is achieved through a combination of manual hardening and the strategic deployment of security suites.
Shopify provides a highly secure foundation, but the risk shifts to the third-party apps and integrations that store owners add to their shops.
Wix operates as a “closed” ecosystem, meaning the platform handles server-side security, but the user remains responsible for content and account integrity.
In 2026, the assumption of eventual compromise is a cornerstone of modern security planning. “Cyber resilience” is the ability of an organization to withstand and recover from an attack with minimal disruption. The most critical component of this resilience is a robust backup and recovery system.
The rule remains the gold standard for data redundancy:
For modern e-commerce and CMS platforms, manual backups are insufficient. Automated, real-time backup solutions ensure that the “Recovery Point Objective” (RPO), the maximum amount of data that can be lost, is kept to a minimum.
Continuous monitoring is necessary to detect a breach in its early stages. File Integrity Monitoring (FIM) tools alert administrators if core system files are modified without authorization, which is a common sign of a “web shell” injection.
Regular malware scanning, performed at least daily, ensures that malicious code is identified and quarantined before it can cause significant damage or lead to the site being blocked by search engines.
| Backup Solution | Best For | Frequency | Key Feature |
| Rewind (Shopify) | Enterprise e-commerce. | Daily / Real-time. | 365-day version history. |
| TinyBackup (Shopify) | Small to medium stores. | Daily / Real-time. | Budget-friendly automated tool. |
| Jetpack (WordPress) | High-activity blogs/stores. | Daily. | Integrated with site performance. |
| Wix Site History | Designers and non-tech users. | Automatic. | Easy version restoration. |
| IDrive | Generic / Multi-platform. | Scheduled. | 5TB value for multiple devices. |
Despite the most advanced technical controls, the human factor remains the leading cause of security breaches, accounting for approximately 80% of incidents.
Social engineering, the psychological manipulation of individuals to perform actions or divulge confidential information, is the primary tactic used to circumvent technical defenses.
The phishing landscape of 2026 includes several specialized variants that website administrators must be trained to recognize.
A culture of security begins with education. Organizations should conduct regular security awareness training that focuses on the latest threats and encourages a “stop and verify” approach. Simulated phishing campaigns provide employees with low-stakes practice in identifying malicious emails.
Furthermore, strict “out-of-band” verification policies must be established. Any request to change financial details, reset high-level passwords, or transfer sensitive data should require verification through a second, trusted channel (e.g., a known phone number), particularly if the request appears to come from an executive.
As the digital landscape continues to shift, the paradigms of website security are evolving toward more proactive and holistic models.
The traditional “castle and moat” security model, where everyone inside the network is trusted, is being replaced by Zero Trust. Under this architecture, no user or device is trusted by default, regardless of their location. Every request is continuously verified based on identity, device health, and behavioral context. This approach significantly reduces the risk of “lateral movement,” where an attacker who has compromised one low-level account can move through the network to reach more sensitive assets.
The arrival of functional quantum computers poses a theoretical but imminent threat to current asymmetric encryption algorithms (like RSA). In 2026, forward-looking organizations are beginning to evaluate quantum-resistant or “post-quantum” cryptographic standards to ensure that data encrypted today remains secure in the decades to come.
The thorough security of a site in 2026 is a continuous process, which requires a holistic approach in technical, procedural, and human aspects. In providing a sound cryptographic base, applying high-level identity control using passkeys and MFA, and applying layered perimeter security such as WAF, administrators can go a long way in reducing the threat of technical exploitation.
However, the rising tide of social engineering and AI-driven impersonation requires a shift in focus toward human resilience and out-of-band verification protocols. Simultaneously, the adoption of a “resilience-first” mindset, characterized by automated backups, recovery testing, and Zero Trust principles, ensures that if a breach does occur, the impact on operations and data integrity is minimized.
Security is not an end but rather a continuous state of preparedness. Ongoing development of web security will demand continuous adjustment, regular check-ins, and the uncompromising adherence to the postulates of data confidentiality, integrity, and availability as the rivals keep developing. The most successful in negotiating the digital future will be organizations that think of security as a strategic pillar and not as a cost to IT.

Hassan Tahir wrote this article, drawing on his experience to clarify WordPress concepts and enhance developer understanding. Through his work, he aims to help both beginners and professionals refine their skills and tackle WordPress projects with greater confidence.